Toward approaches to big data analysis for terroristic behavior identification: child soldiers in illegal armed groups during the conflict in Donbas region (East Ukraine)
Abstract
В статті розглядається підхід до використання великих даних (контенту соціальних мереж) для розуміння соціальної поведінки в зонах конфлікту і аналізу групової динаміки в нелегальних озброєних угрпуваннях. Аналіз спрямовано на ідентифікацію неповнолітніх учасників збройних формувань. Запропоновано ймовірнісний і стохастичний методи аналізу, а також класифікації, кількості, структури і динаміки нелегальних озброєних угрупувань. Використано дані, що стосуються антитерористичної операції на Донбасі (Східна Україна, 2014-2015 рік). Обчислено кількісний розподіл учасників незаконних збройних формувань за віком, гендерним складом, походженням і соціальним статусом. Запропоновано висновки щодо доцільності застосування описаного методу в кримінологічній практиці, а також можливості інтерпретації отриманих результатів в контексті вивчення тероризму.
In criminological practice and research of terrorism, there are many cases requiring application of sophisticated scientific instruments. Not only at the stage of analysis of evidences, but also at the preliminary stages, in particular, at the stage of crime identification.
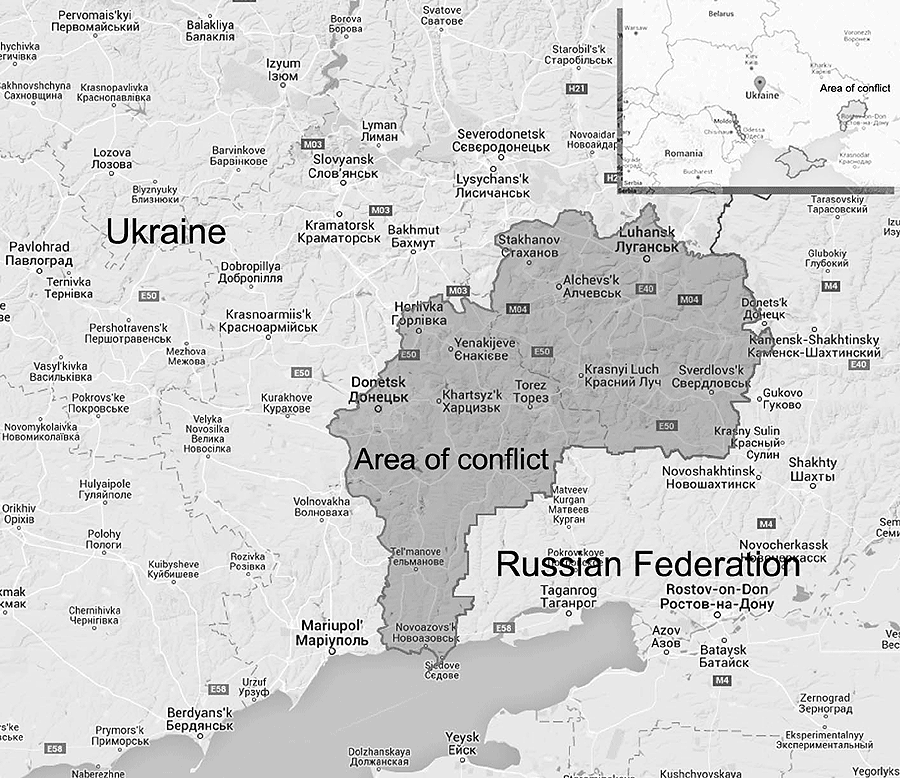
Description of criminal activity and identification of a crime is a challenge in some cases, for example, in the areas of crisis, conflict, and fighting. This is due to significant limitations of existing information and data available.
In such cases it is necessary to use many different sources of information, including social networks, with adapted statistical approaches to assessment of this data. Correct statistical methods of data collection, analysis, filtering and regularization in such cases are critical.
Obtained with the mathematical methods, robust spatial-temporal distributions of data could be used to define the event and to identify a crime.
Social networks reflect the motivations of the behaviour of different groups of society and varied social environments (Wasserman, Galaskiewicz, 1994). So, because of the large scope, it is a good base for sociometrics and behavior analysis (Krause, Croft, James, 2007). However, formal numerical methods of social network data analysis are still not sufficiently developed for a wide range of important cases, in particular for crisis management (Lerbinger, 2012) and conflict analysis (Scott, 2012).
The task of extraction of structured distributions of data regularized by determining parameters from the large sets of non-structured data is solving. The algorithm based on specifics of dig data distribution, and on data source characteristics (e.g. group behavior). Realization of this approach aimed to detection of stable indicators of criminal and/or terroristic activity. At the same time the analyzed data and cyber activity, producing it might be legal in most cases (if propaganda is beyond our scope).
The proposed algorithm allows to analyze the content of social networks on the base of the set of selected indicators. These indicators allow to control the social dynamics of different social groups represented in social networks and analyze their behavior, including identification of evidences of terrorism.
Assuredly, social media activity in itself is not a terrorist in the strict sense, since it is not a method of achieving of political goals using a direct violence (physical or psychological). However, an important evidence of terrorism is its demonstrative character. The attack requires a nationwide, or ideally a global audience. Therefore, an information component of terroristic activity is extremely important.
In particular, there are several main objectives of the information campaign of terrorist activity. This is propaganda of impotence of central power and calls for the creation of alternative authorities. Second, this is making the precedents of active disobedience and military confrontation with a central power. Third, this is dissemination of appeals to the people to join the active opposition to the authorities, glorification of terrorists, promoting their ideas and lifestyle. Also, positive information about terrorism activates any local power and social mood, the opposed government, including distanced from terrorist tactics before. Additionally, the attack is treated as an indisputable sign of the acute crisis in the society. All this is pushing the society and the power to make concessions to political forces that use terrorist tactics. Terrorism and its propaganda make strikes on the economy, reduces the investment attractiveness of the country, degrades the image of the country, pushing the country to the radicalization of the political course, to authoritarian forms of government (often this evolution is a purpose of terrorists).
Terrorism is the most dangerous and the most effective (by the criterion of the invested resources / result) way to the political destabilization of society. And also this is one of the most effective destabilizing tools of the enemy within the modern hybrid conflicts.
At the same time, the use of terrorist tactics presupposes a set of specific socio-cultural and political characteristics of the target society. Terrorism is a phenomenon inherent to the crisis stage of the modernization of society. Commonly, the completion of modernization transformations removes grounds for terrorism. Terrorism occurs at the boundaries of cultures and periods of history.
Terrorism is an indicator of the crisis processes. This is the "emergency channel" of feedback between society and government, between a separate part of the community and society as a whole. It indicates to the acute trouble in a certain area of social space. In this respect, terrorism have not a pure power, police solutions. Localization and suppression of terrorists is only a part of the job. Another part involves political, social and cultural changes, which should remove the reasons for the radicalization of society and base of the terrorism.
In this context, the analysis of social dynamics and the behavior of social groups is becoming an important factor in the control of terrorist activities. Not only and not so much as for the identification of the criminals, but the identification of the crime, the identification of its social base, to determine the causes and driving forces of terrorism is a task to be solved by approaches proposed in this study.